Difference between revisions of "TCP/IP"
(→TCP/IP Stack) |
(→TRC PowerPoint) |
||
| (17 intermediate revisions by 2 users not shown) | |||
| Line 1: | Line 1: | ||
| − | ==What is a protocol | + | =Overview= |
| + | ===CraigNDave=== | ||
| + | <youtube>https://www.youtube.com/watch?v=R5aJSWucbe8&index=1&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=R5aJSWucbe8&index=1&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm | ||
| + | |||
| + | ===Computer Science Tutor=== | ||
| + | <youtube>MVihcigDlbA</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=MVihcigDlbA&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=36 | ||
| + | |||
| + | <youtube>7LfTWbOp5vU</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=7LfTWbOp5vU&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=37 | ||
| + | |||
| + | =What is a protocol= | ||
A protocol is a set of rules, using protocols will allow 2 devices using the same protocol to communicate effectively. Many protocols are used, but they all perform a specific task. | A protocol is a set of rules, using protocols will allow 2 devices using the same protocol to communicate effectively. Many protocols are used, but they all perform a specific task. | ||
=TCP/IP Stack= | =TCP/IP Stack= | ||
| − | TCP/IP stands for Transmission Control Protocol / Internet Protocol, it defines how data packets are transmitted over a network. TCP is used to break up the data into packets, it will keep track of the packets, and it will re-assemble the packets. IP is used to | + | TCP/IP stands for Transmission Control Protocol / Internet Protocol, it defines how data packets are transmitted over a network. TCP is used to break up the data into packets, it will keep track of the packets, and it will re-assemble the packets. IP is used to deliver each individual packet. |
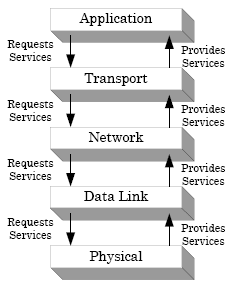
| − | TCP/IP is a stack of protocols because it includes several layers and each layer uses a number of different protocols. Each layer will wrap the data passed to it, with the appropriate information for the layer. When received the layers are unwrapped by each layer. The physical layer | + | TCP/IP is a stack of protocols because it includes several layers and each layer uses a number of different protocols. Each layer will wrap the data passed to it, with the appropriate information for the layer. When received the layers are unwrapped by each layer. Each layer on the sending device is logically linked to the same layer of the receiving device and so on. The physical layer are the actual network devices, such as Ethernet Cables. |
[[File:tcpip.gif]] | [[File:tcpip.gif]] | ||
| Line 33: | Line 48: | ||
==Network layer== | ==Network layer== | ||
| + | Sometimes referred to as the internet or IP layer, it adds the source and destination IP addresses to each packet. This combination of IP address and the port number forms a socket. | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Packet 1 of 3 !! Packet 2 of 3 !! Packet 3 of 3 | ||
| + | |- | ||
| + | | The quick brown || fox jumps over|| the lazy dog | ||
| + | |- | ||
| + | | Port 80 || Port 80 || Port 80 | ||
| + | |- | ||
| + | | 89.203.11.63 - 123.21.139.2|| 89.203.11.63 - 123.21.139.2|| 89.203.11.63 - 123.21.139.2 | ||
| + | |} | ||
==Link layer== | ==Link layer== | ||
| + | Adds the MAC (Media Access Control) Addresses identifying the Network Interface Controllers of the sender and the destination. This allows the data to get to the specific device once it has reached the required IP address. The destination MAC address is changed for each hop of the journey, the original MAC address will therefore be the address of the first router the data is forwarded to. | ||
| + | |||
| + | {| class="wikitable" | ||
| + | |- | ||
| + | ! Packet 1 of 3 !! Packet 2 of 3 !! Packet 3 of 3 | ||
| + | |- | ||
| + | | The quick brown || fox jumps over|| the lazy dog | ||
| + | |- | ||
| + | | Port 80 || Port 80 || Port 80 | ||
| + | |- | ||
| + | | 89.203.11.63 - 123.21.139.2|| 89.203.11.63 - 123.21.139.2|| 89.203.11.63 - 123.21.139.2 | ||
| + | |- | ||
| + | | 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 || 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 || 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 | ||
| + | |} | ||
=Ports= | =Ports= | ||
| Line 44: | Line 85: | ||
==Well known port numbers== | ==Well known port numbers== | ||
Well Known port numbers are important because if everyone sticks to the numbers you can connect without any issues. If you change the port number of your webserver to 85 for example, nobody would be able to connect unless they knew to use 85 instead of 80. | Well Known port numbers are important because if everyone sticks to the numbers you can connect without any issues. If you change the port number of your webserver to 85 for example, nobody would be able to connect unless they knew to use 85 instead of 80. | ||
| + | |||
| + | <youtube>https://www.youtube.com/watch?v=g-S875o-dKM&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=2</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=g-S875o-dKM&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=2 | ||
The common port numbers are: | The common port numbers are: | ||
| Line 64: | Line 109: | ||
=Protocols= | =Protocols= | ||
| + | <youtube>https://www.youtube.com/watch?v=n8anpB3dvsQ&index=3&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=n8anpB3dvsQ&index=3&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm | ||
| + | |||
The most common are: | The most common are: | ||
| − | ==HTTP== | + | ==Web== |
| + | <youtube>https://www.youtube.com/watch?v=63Uk7qiaq_4&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=7</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=63Uk7qiaq_4&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=7 | ||
| + | |||
| + | ===HTTP=== | ||
'''H'''yper '''T'''ext '''T'''ransfer '''P'''rotocol, most often found at the beginning of URLs, is used to transfer an user to a web address that is specified via the domain. This uses port 80, | '''H'''yper '''T'''ext '''T'''ransfer '''P'''rotocol, most often found at the beginning of URLs, is used to transfer an user to a web address that is specified via the domain. This uses port 80, | ||
| − | ==HTTPS== | + | ===HTTPS=== |
A verified, '''s'''ecure version of '''HTTP'''. This ensures the user that the website they are on is safe and well protected. This uses port 443. | A verified, '''s'''ecure version of '''HTTP'''. This ensures the user that the website they are on is safe and well protected. This uses port 443. | ||
==FTP== | ==FTP== | ||
'''F'''ile '''T'''ransfer '''P'''rotocol. This allows you to download / upload files to a server, for example you would upload your websites pages to your webserver using FTP. FTP uses port 21. | '''F'''ile '''T'''ransfer '''P'''rotocol. This allows you to download / upload files to a server, for example you would upload your websites pages to your webserver using FTP. FTP uses port 21. | ||
| + | |||
| + | <youtube>https://www.youtube.com/watch?v=ndqIayKWNp0&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=4</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=ndqIayKWNp0&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=4 | ||
==SSH== | ==SSH== | ||
'''S'''ecure '''Sh'''ell protocol. This protocol allows remote access to a computer, this could be used to perform admin tasks on a server. You will only have command line access to the computer. SSH is also designed for operating securely over an unsecure network. SSH uses port 22, this was deliberately chosen because it was created to potentially use instead of Telnet or FTP. | '''S'''ecure '''Sh'''ell protocol. This protocol allows remote access to a computer, this could be used to perform admin tasks on a server. You will only have command line access to the computer. SSH is also designed for operating securely over an unsecure network. SSH uses port 22, this was deliberately chosen because it was created to potentially use instead of Telnet or FTP. | ||
| + | |||
| + | <youtube>https://www.youtube.com/watch?v=vFq3C3jiZLw&index=5&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=vFq3C3jiZLw&index=5&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm | ||
==TELNET== | ==TELNET== | ||
Allows a user to log into a remote computer over the interlinking network. Similar to but predates SSH. Telnet uses port 23. | Allows a user to log into a remote computer over the interlinking network. Similar to but predates SSH. Telnet uses port 23. | ||
| − | ==POP3== | + | ==Email== |
| + | <youtube>https://www.youtube.com/watch?v=H17xGNGdZIM&index=6&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm</youtube> | ||
| + | |||
| + | https://www.youtube.com/watch?v=H17xGNGdZIM&index=6&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm | ||
| + | |||
| + | ===POP3=== | ||
'''P'''ost '''O'''ffice '''P'''rotocol, version '''3'''. Used to receive incoming emails from an email server. This uses port 110. | '''P'''ost '''O'''ffice '''P'''rotocol, version '''3'''. Used to receive incoming emails from an email server. This uses port 110. | ||
| − | ==SMTP== | + | ===SMTP=== |
Simple Mail Transfer Protocol. This is used to send emails, it uses port 25. | Simple Mail Transfer Protocol. This is used to send emails, it uses port 25. | ||
Latest revision as of 08:21, 23 August 2023
Overview
CraigNDave
https://www.youtube.com/watch?v=R5aJSWucbe8&index=1&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm
Computer Science Tutor
https://www.youtube.com/watch?v=MVihcigDlbA&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=36
https://www.youtube.com/watch?v=7LfTWbOp5vU&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=37
What is a protocol
A protocol is a set of rules, using protocols will allow 2 devices using the same protocol to communicate effectively. Many protocols are used, but they all perform a specific task.
TCP/IP Stack
TCP/IP stands for Transmission Control Protocol / Internet Protocol, it defines how data packets are transmitted over a network. TCP is used to break up the data into packets, it will keep track of the packets, and it will re-assemble the packets. IP is used to deliver each individual packet.
TCP/IP is a stack of protocols because it includes several layers and each layer uses a number of different protocols. Each layer will wrap the data passed to it, with the appropriate information for the layer. When received the layers are unwrapped by each layer. Each layer on the sending device is logically linked to the same layer of the receiving device and so on. The physical layer are the actual network devices, such as Ethernet Cables.
Application layer
The application layer sits at the top of the stack and uses protocols relating to the application being used to transmit the data over a network. Incoming and outgoing data are converted from one presentation format to another, the original data and the appropriate format for the application layer protocol.
Application layer protocols include: HTTP, FTP, SSH, POP3, SMTP etc.
For example the data could be:
The quick brown foxes jumps over the lazy dog
Transport layer
The transport layer uses TCP to establish an end-to-end connection with the recipient computer. The data is then split into packets and labelled with the packet number and the port number through which the packet should route. This ensures it is handled by the correct application.
If any packets go astray during the connection the transport layer will request for them to be re-transmitted.
The above example could be broken into packets:
| Packet 1 of 3 | Packet 2 of 3 | Packet 3 of 3 |
|---|---|---|
| The quick brown | fox jumps over | the lazy dog |
| Port 80 | Port 80 | Port 80 |
Network layer
Sometimes referred to as the internet or IP layer, it adds the source and destination IP addresses to each packet. This combination of IP address and the port number forms a socket.
| Packet 1 of 3 | Packet 2 of 3 | Packet 3 of 3 |
|---|---|---|
| The quick brown | fox jumps over | the lazy dog |
| Port 80 | Port 80 | Port 80 |
| 89.203.11.63 - 123.21.139.2 | 89.203.11.63 - 123.21.139.2 | 89.203.11.63 - 123.21.139.2 |
Link layer
Adds the MAC (Media Access Control) Addresses identifying the Network Interface Controllers of the sender and the destination. This allows the data to get to the specific device once it has reached the required IP address. The destination MAC address is changed for each hop of the journey, the original MAC address will therefore be the address of the first router the data is forwarded to.
| Packet 1 of 3 | Packet 2 of 3 | Packet 3 of 3 |
|---|---|---|
| The quick brown | fox jumps over | the lazy dog |
| Port 80 | Port 80 | Port 80 |
| 89.203.11.63 - 123.21.139.2 | 89.203.11.63 - 123.21.139.2 | 89.203.11.63 - 123.21.139.2 |
| 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 | 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 | 00:A0:C9:14:C8:29 - 10:B0:E5:19:C1:B9 |
Ports
An addressable location on a network that links to a process or application. A port number is a way to identify a specific process to which an Internet or other network message is to be forwarded when it arrives at a server. The port number is a 16 bit integer, The well-known ports cover the range of possible port numbers from 0 through 1023. The registered ports are numbered from 1024 through 49151. The remaining ports, referred to as dynamic ports or private ports, are numbered from 49152 through 65535.
Why we need them
When an application communicates over a certain port, it expects a specific type of connection with another system or application. Specifying port numbers ensure two systems communicate correctly. While it is possible for two systems to communicate over any given port, it can cause interference if other data is being transmitted on the same port. The application will also listen to the port for incoming data.
Well known port numbers
Well Known port numbers are important because if everyone sticks to the numbers you can connect without any issues. If you change the port number of your webserver to 85 for example, nobody would be able to connect unless they knew to use 85 instead of 80.
https://www.youtube.com/watch?v=g-S875o-dKM&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=2
The common port numbers are:
- 21 FTP
- 22 SSH
- 23 Telnet
- 25 SMTP
- 80 HTTP
- 110 POP3
- 443 HTTPS
Socket
A socket is an endpoint in a communication, it identifies an application and device. It is the IP address with a Port number, so this would be a socket:
192.168.1.150 : 80
Where as, this is just an IP:
192.168.1.150
Protocols
https://www.youtube.com/watch?v=n8anpB3dvsQ&index=3&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm
The most common are:
Web
https://www.youtube.com/watch?v=63Uk7qiaq_4&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=7
HTTP
Hyper Text Transfer Protocol, most often found at the beginning of URLs, is used to transfer an user to a web address that is specified via the domain. This uses port 80,
HTTPS
A verified, secure version of HTTP. This ensures the user that the website they are on is safe and well protected. This uses port 443.
FTP
File Transfer Protocol. This allows you to download / upload files to a server, for example you would upload your websites pages to your webserver using FTP. FTP uses port 21.
https://www.youtube.com/watch?v=ndqIayKWNp0&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm&index=4
SSH
Secure Shell protocol. This protocol allows remote access to a computer, this could be used to perform admin tasks on a server. You will only have command line access to the computer. SSH is also designed for operating securely over an unsecure network. SSH uses port 22, this was deliberately chosen because it was created to potentially use instead of Telnet or FTP.
https://www.youtube.com/watch?v=vFq3C3jiZLw&index=5&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm
TELNET
Allows a user to log into a remote computer over the interlinking network. Similar to but predates SSH. Telnet uses port 23.
https://www.youtube.com/watch?v=H17xGNGdZIM&index=6&list=PLCiOXwirraUCw0BWhWk_5rInOWRnzf8Xm
POP3
Post Office Protocol, version 3. Used to receive incoming emails from an email server. This uses port 110.
SMTP
Simple Mail Transfer Protocol. This is used to send emails, it uses port 25.