Difference between revisions of "Wireless Networking"
(→Question 2) |
(→Overview) |
||
| (17 intermediate revisions by 6 users not shown) | |||
| Line 12: | Line 12: | ||
https://www.youtube.com/watch?v=Z_R4GubNuhg&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=30 | https://www.youtube.com/watch?v=Z_R4GubNuhg&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=30 | ||
| − | ===TRC | + | ===TRC Video=== |
| − | + | <youtube>https://www.youtube.com/watch?v=8TBVGxf81DA</youtube> | |
| + | |||
| + | https://www.youtube.com/watch?v=8TBVGxf81DA | ||
=Devices= | =Devices= | ||
| Line 88: | Line 90: | ||
=Revision Questions= | =Revision Questions= | ||
| − | |||
<quiz display=simple> | <quiz display=simple> | ||
| − | { | + | { What hardware component does each device need to be able to be connected to a wireless network? |
| − | |type="()"} | + | | type="()" } |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | - WAC | |
| − | + | - WMIC | |
| − | - | + | - WAP |
| − | + | + WNIC | |
| − | - | ||
| − | |||
| − | + | ||
| + | {What is a station composed of in terms of wireless networking? | ||
| + | |type="[]"} | ||
| + | - A table. | ||
| + | || ... | ||
| + | + A device. | ||
| + | || Correct | ||
| + | - An ethernet cable. | ||
| + | || "Wireless networking" | ||
| + | - Wireless Access Point | ||
| + | || Incorrect, a WAP allows other devices to connect to the network | ||
| + | + A network interface card | ||
| + | || Correct. A NIC allows for a device to connect to networks | ||
| + | {What does SSID stand for? | ||
| + | | type="()"} | ||
| + | - Salad Sub including Daikon | ||
| + | - Solid State identification | ||
| + | + Service set identifier | ||
| + | - Super Safe Intercredible Democracy | ||
| + | {What is the role of the SSID: | ||
| + | | type = "[]"} | ||
| + | + Name given to the router | ||
| + | || correct answer | ||
| + | - Allows access to router when there are multiple devices | ||
| + | || Wrong answer | ||
| + | + Displays when scanned by a device | ||
| + | || Correct answer | ||
| − | + | Select the amount of channels that's provided by 2.4ghz and 5ghz? | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| type="()" } | | type="()" } | ||
- 2.4ghz has 27 channels and 5ghz has 12 channels. | - 2.4ghz has 27 channels and 5ghz has 12 channels. | ||
| Line 130: | Line 141: | ||
|| ... | || ... | ||
| − | + | {what does RTS stand for? | |
| + | | type="()"} | ||
| + | - Real time strategy | ||
| + | - Royal Television Society | ||
| + | + Request to send | ||
| + | - Rich Taxes (are) Stupid | ||
| − | = | + | {what does CTS stand for? |
| − | + | | type="()"} | |
| − | + | - Clear time strategy | |
| − | + | - Central Television Society | |
| + | + Clear to send | ||
| + | - Corporation Taxes (are) Stupid | ||
| − | { | + | { Which one of these would make a network more secure? |
| − | |type="[]"} | + | | type="[]" } |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| + | + Use a MAC address whitelist. | ||
| + | ||Correct answer. | ||
| + | + Change and remove SSID from being shared. | ||
| + | ||Correct answer. | ||
| + | + Use WPA/WPA2. | ||
| + | ||Correct answer. | ||
| + | - Wrap the network in bubble wrap. | ||
| + | ||The correct answer were the other three answers. | ||
| − | + | { Which are the benefits of WPA/WPA2 over WEP? | |
| − | + | | type="[]" } | |
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | | type=" | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | + | + WEP typically uses a lower bit key, WPA/WPA2 uses a higher bit key . | |
| + | ||Correct answer. | ||
| + | + In WEP the key is constant, WPA/WPA2 generates a key for each packet. | ||
| + | ||Correct answer. | ||
| + | - WPA/WPA2 uses lower bit key, WEP uses a higher bit key. | ||
| + | ||The correct answers were WEP typically uses a lower bit key, WPA/WPA2 uses a higher bit key, in WEP the key is constant, WPA/WPA2 generates a key for each packet. | ||
| + | - In WPA/WPA2 the key is constant, WEP generates a key for each packet. | ||
| + | ||The correct answers were WEP typically uses a lower bit key, WPA/WPA2 uses a higher bit key, in WEP the key is constant, WPA/WPA2 generates a key for each packet. | ||
| − | |||
| − | |||
| − | |||
| − | |||
{ Describe the various security measures, other then logging in, that a school or business might have put in place to prevent anyone unauthorised from connecting to the network. | { Describe the various security measures, other then logging in, that a school or business might have put in place to prevent anyone unauthorised from connecting to the network. | ||
| type="[]" } | | type="[]" } | ||
| Line 185: | Line 189: | ||
+ Secure the network using WPA/WPA2 | + Secure the network using WPA/WPA2 | ||
+ Hide the SSID | + Hide the SSID | ||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
| − | |||
{What does white listing devices do: | {What does white listing devices do: | ||
| Line 215: | Line 197: | ||
|| right answer | || right answer | ||
| + | {what does disabling SSID broadcasting do? | ||
| + | |type="()"} | ||
| + | -only allows MAC addresses on a stored list to access | ||
| + | ||this is MAC address whitelisting | ||
| + | -key to packet encrypting | ||
| + | ||WPA/WPA2 | ||
| + | +must pre know the network to connect, will not appear; not broadcasted | ||
| + | |||
| + | { When considering WPA/WPA2 What does a per-packet key entail? | ||
| + | | type="()" } | ||
| + | - A key split into many packets. | ||
| + | || Incorrect. A per packet key has a different key for each packet. | ||
| + | + A different key for each packet. | ||
| + | || Correct! | ||
| + | - A single key per packet | ||
| + | || Incorrect. A per packet key has a different key for each packet. | ||
| + | - The key has no packets | ||
| + | || Incorrect. A per packet key has a different key for each packet. | ||
</quiz> | </quiz> | ||
| − | |||
| − | |||
Latest revision as of 09:30, 23 August 2023
Contents
Overview
Wireless networking is used to wirelessly communicate devices to a network. Data is transmitted using radio waves. The Wi-Fi Alliance establish international standards to allow interoperability and backwards compatibility.
CraigNDave
https://www.youtube.com/watch?v=03cdhk8WruE&list=PLCiOXwirraUDvVsza-xO2mMwW9QBIa_FG&index=3
Computer Science Tutor
https://www.youtube.com/watch?v=Z_R4GubNuhg&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=30
TRC Video
https://www.youtube.com/watch?v=8TBVGxf81DA
Devices
These are connected by using a WAP (Wireless Access Point), this is a bridge between a wireless network and a wired network. They broadcast a wireless signal which other devices can connect to, all the devices share the bandwidth of the access point. The Access Point is normally connected to a single wired network port. In the home this could be packaged with a router and a network switch, but can also be a stand alone device.
A receiving device called a Wireless Network Interface Card. These can be added to a mobile device or a computer by using either a Wi-Fi dongle or a Wi-Fi PCIe Card. It is the device used to connect to a wireless network, receive and transmit data wirelessly.
A Station is a combination of a device and a wireless networking interface card.
Standards / Technologies
These are a few different types of network technologies. The most common and newest version is 802.11ac but there are different types including 802.11a/b/g/n/ac/ac/ab. Speeds have increased from approximately 11mbps to 500mbps.
Distance
Distance affects the signal of the Wi-Fi, if the signal is indoors it can spread to a distance of 50-70m and outdoors it can spread to a distance of 250m. It is weaker indoors because of interference like doors, walls, pipework and microwaves.
SSID
Each network is set a SSID (Service Set Identification). This is the name that is associated with a network. When a device is trying to connect to a network, the device will search for a network . and that network will report back with its SSID. Some networks don't broadcast there SSID. This is so that devices can't find the network during a search, they can still connect to the network but they will need to know it exists.
MAC Address
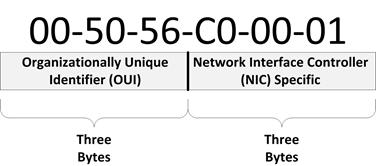
A MAC (Media Access Control) address is a group of hexadecimal digits that contain information about that device that broadcasts data. the first three groups represents the manufacturer (or manufacturer & type of device) and the last three groups represent your actual device.
The purpose of the MAC Address is to uniquely identify your device, any data is sent to the MAC Address at a specific IP Address. Your device may have several MAC Addresses, one for Wi-Fi, one for Bluetooth, and one for NFC.
Protocols
https://www.youtube.com/watch?v=WpSZBu9i108&list=PLCiOXwirraUDvVsza-xO2mMwW9QBIa_FG&index=4
CSMA/CA
Computer Science Tutor
https://www.youtube.com/watch?v=My4VDzviiNg&list=PL04uZ7242_M6O_6ITD6ncf7EonVHyBeCm&index=31
CSMA/CA without RTS/CTS
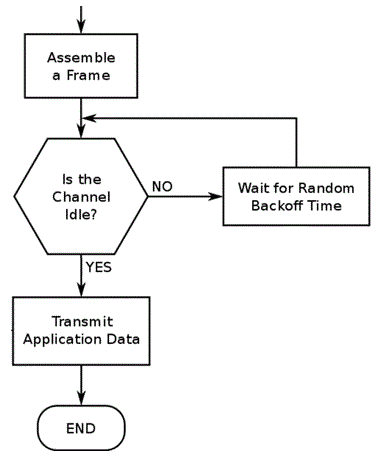
Ethernet uses the CSMA/CD protocol which detects if a data collision has occurred, it will stop the transmission on the colliding devices and each will wait a random amount of time before resending.
CSMA/CA actually checks the communication channel is idle before sending any data. This will prevent collisions.
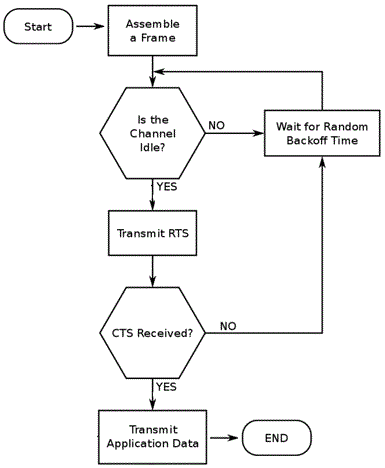
CSMA/CA with RTS/CTS
RTS/CTS adds an extra layer onto CSMA/CA, by checking if the receiving machine is ready to receive data. A Request To Send is transmitted, and when ready the receiver will transmit a Clear To Send.
Frequency & Channels
2 different frequencies are used for Wi-Fi, The old Wi-Fi frequency is 2.4Ghz which is what all Wi-Fi capable devices can use. This frequency has become very crowded and is used by other technology such as microwaves etc.
A new frequency as been approved, the 5Ghz frequency cannot be accessed by older devices which only support the 2.4Ghz frequency. The main benefit of this is that not many devices use this new technology so that means that there wont be as much interference hence better speeds.
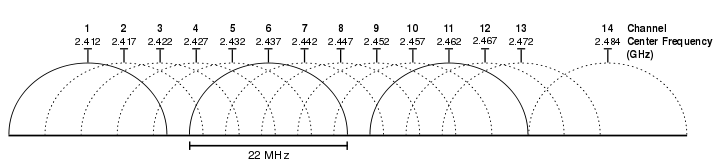
The 2.4Ghz frequency is broken up into approximately 12 channels that can be used, and the 5Ghz frequency is broken up into more channels and in Europe 27 channels are usable. Channels are required because different wireless networks can overlap, and by using a different channel different wireless networks can operate.
However the image above shows how the channels on the 2.4Ghz frequency can interfere with each other. Having adjacent channels is never a good idea because too much interference is generated, there should always be atleast 2 channels in between.
In the home situation your wireless router creates a Wi-Fi network which overlaps with the wireless network next door or even from across the road. Imagine the situation in densely populated areas such has the Centre of London or Manchester.
Wireless Network Security
There are many different ways that you can secure a network.
- Change the default SSID to your own
- Hide the SSID
- Create a whitelist to only allow certain devices to connect to the network
- Secure the network with a password using WPA/WPA2
WPA/WPA2
WPA or Wi-Fi Protected Access is a protocol that secures a Wi-Fi network. It was developed by the Wi-Fi Alliance to secure wireless networks. WPA was rolled out in 2003 and then WPA2 was introduced in 2004 improving upon WPA.
It replaced WEP which used a single key for all data packets, however WPA/WPA2 use a different key for each packet.